At a panel presentation/discussion titled "Hacked: TheImplications of a Cyber Breach," hosted by Travelers in New YorkCity, Timothy Francis, enterprise lead for Cyber insurance, notedthat although most of the cyber breaches that make the headlinesare from large, national companies, the smaller breaches of localcompanies are far greater in number.
|Francis noted that 62% of cyber-breach victims are small tomid-size businesses, which are at the greatest risk for an attack.Their level of preparation is low, and the costs of customernotification alone can be enough to do a small company irreparablefinancial harm.
|Mark C. Greisiger, president of NetDiligence, which providescyber risk assessment and data-breach crisis services, noted thathealthcare and financial services are the two most affectedindustries at the moment. Those small to mid-sized financialservices businesses include many of the insurance agents andbrokers in the U.S.
|A good many data breaches go undetected and others are willfullyunreported, Greisiger observed. Often, the data breach incident isa denial of service attack, which companies don't report becausethey aren't obligated by law to do so. According to Francis, thereare 34,529 known computer sercurity incidents per day inthe U.S. How many more are unknown?
|
(Photo: Shutterstock/KrasimiraNevenova)
|All businesses arevulnerable
|The average per-breach cost for legal fees is $690,000, whilefor larger companies the breach claims cost can amount to $3million per event or more. That per-breach estimate is skewedtoward the amount of information stolen from healthcare and smallto mid-size companies, Greisiger added, but companies withoutinsurance can expect to pay significantly more, primarily becausethey generally don't have instant access to the various experts(that is, the "tiger team" with pre-negotiated rates) needed tomitigate the breach in a timely manner after it occurs.
|These include a forensics team to conduct investigations, publicrelations representatives, a call center to deal with customerfallout, and legal counsel, including a "breach coach" whose job itis to work with the client to help ascertain exactly what wasstolen. Businesses that suffer a breach that don't have insuranceprotections can expect to pay three times as much for theseservices, and even then, are often doing so to vendors that haven'tbeen vetted and selected by a major insurer.
|Regardless of size, however, all businesses should considerthemselves vulnerable. In Francis' view, "It's not if abreach will occur, it's when."
|Greisiger also suggested that businesses learn to think of theissue as one of "privacy management," explaining that the term"cyber" applies to all media and all devices, including personallyidentifiable information that your employees might have access toon their tablets or smartphones.
|A few years ago, lost laptops were the leading cause of the lossof data and hacking, according to Greisiger. That seems to havetapered off, primarily because of better employee training. Now,the issue has become one of improper data collection or improperuse of the personally identifiable information collected.
| 
(Photo: Shutterstock/Antonio Guillem)
|'Main Street' event
|John F. Mullen, the managing partner of the Philadelphiaregional office and chair of the U.S. Data Privacy and NetworkSecurity Group with Lewis Brisbois Bisgaard & Smith, suggestedthat businesses think of a cyber breach like a burglary: You ownthe data as if it were a tangible object that can be stolen, andyou have a duty to protect it.
|Storing data in the cloud doesn't eliminate your responsibility,Mullen pointed out: "You own the data because you got it first." Aclient can't fully transfer the risk of safeguarding the data toits cloud storage company. Even though a company might trust itscloud storage vendor, that data may be vulnerable when that vendoroutsources storage to another cloud storage vendor.
|In additional to the business interruption issues, Mullenpointed out that it can take from two months to two years todetermine whether your business will be fined for the breach, andby how many state or federal regulators. The high dollar costs,coupled with the distraction of dealing with the breach, can beenough to put a small to mid-sized company out of business.
|Francis noted that agents and brokers need to convey the needfor cyber risk insurance to their small to mid-sized clients. Theinsurance industry also has to do a better job of educating agentsand brokers as well as raising awareness of the issue forthemselves and their clients. If not, the business that closescould be theirs.
|Click "Next" to see statistics about the number of smallbusinesses in the U.S. and the percentage that are concerned aboutspecific cyber risks.
|By the numbers
|The Officeof Advocacy of the Small Business Administration defines asmall business as an independent business having fewer than 500employees, which covers the majority of businesses in the U.S.
|Small businesses make up:
- 99.7 percent of U.S. employer firms,
- 63 percent of net new private-sector jobs,
- 48.5 percent of private-sector employment,
- 42 percent of private-sector payroll,
- 46 percent of private-sector output,
- 37 percent of high-tech employment,
- 98 percent of firms exporting goods, and
- 33 percent of exporting value.
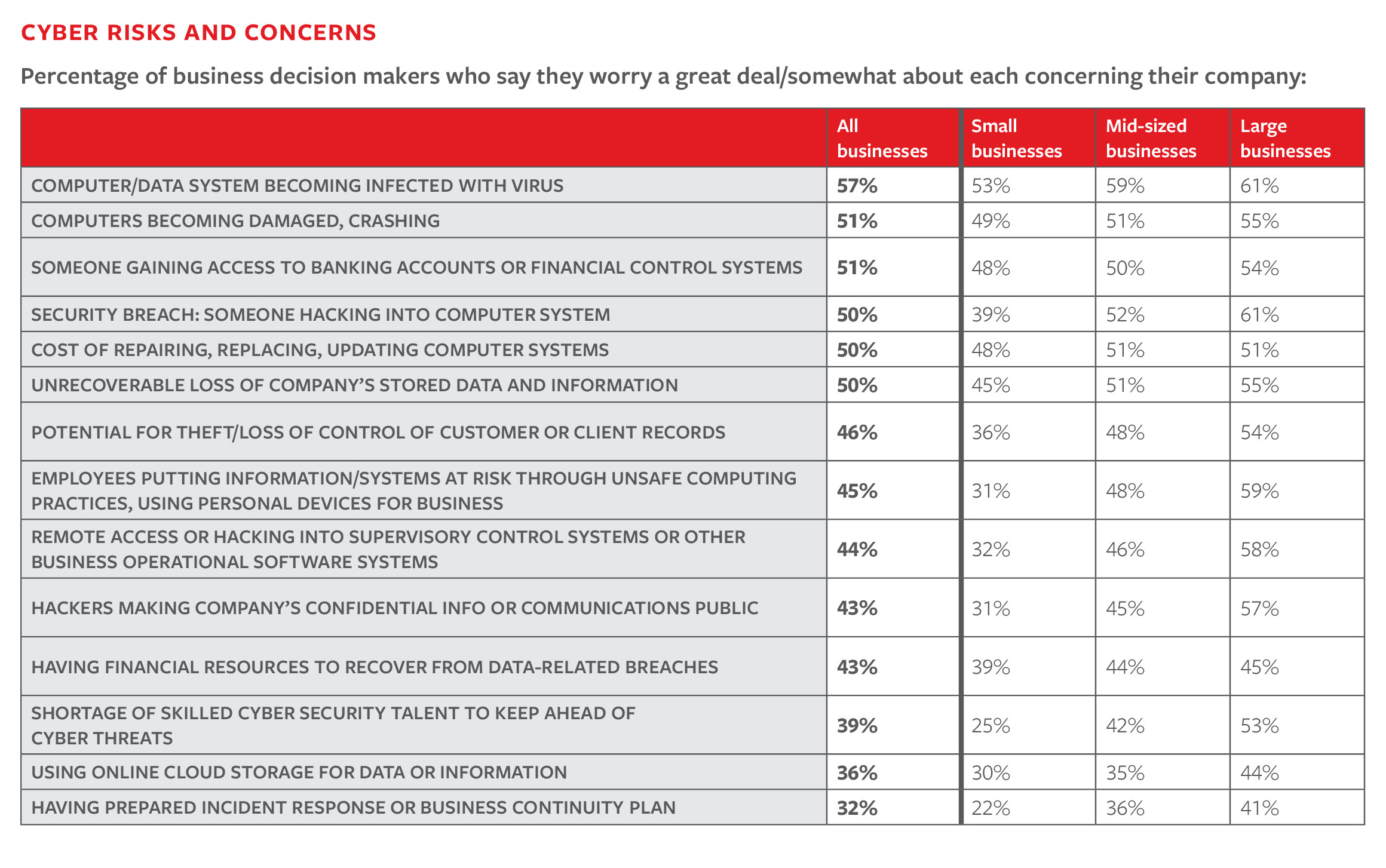
Here is a list of cyber risks and concerns and the percentage ofbusiness decision-makers that worry about each one having an impacton their company. (Click to enlarge.)
||Source: Travelers/NetDiligence
Want to continue reading?
Become a Free PropertyCasualty360 Digital Reader
Your access to unlimited PropertyCasualty360 content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- All PropertyCasualty360.com news coverage, best practices, and in-depth analysis.
- Educational webcasts, resources from industry leaders, and informative newsletters.
- Other award-winning websites including BenefitsPRO.com and ThinkAdvisor.com.
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.