On Dec. 23, the last thing holiday shoppers at Target wanted tobe thinking about was having their credit-card informationcompromised. But that was one luxury no one on hand couldafford.
|"We don't know yet," one harried store manager in Staten Islandpainfully admitted to one especially persistent elderly womandemanding answers about what data thieves now knew. Was she safe?Could she continue to shop? Should she? How badly had the retailgiant's consumer database been compromised? No one could say forcertain.
|Target's data breach, involving the theft of at least 40 millioncredit and debit card records and personal information of 70million customers, dominated headlines after it was publiclyrevealed in late December 2013, driving home the need for betterprotections against the growing specter of cyber crime. But if theTarget incident was unusually large in scope, it was by no meansunique: The Identity Theft Resource Center, which has tracked databreaches since 2005, reported 619 publicly disclosed breaches in2013—a 30% increase over 2012.
|As the number of data breaches and cyber crime increasinglygrows over the years, so has interest in cyber liability coverageby businesses—a trend that shows no sign of slowing. According toBetterley Risk Consultants Inc., cyber has grown to a $2 billionmarket (twice what it was in 2012), with the majority of carriersreporting premium growth between 10% and 25% and several reporting25% to 50% and more.
|"The impact of the Target breach on the cyber sector is that itwill take a coverage that had already been growing in demand andmake it even more so," predicts Christine Marciano, president ofCyber Data Risk Managers, an agency that specializes in dataprivacy and cyber liability risk.
|Unlike a few years ago, she adds, companies now are growing moreserious about this area of cover: "You'd be hard-pressed to find anorganization that hasn't explored ways to budget for cyber if theyhaven't purchased it already."
|Previously, the process of buying cyber cover spanned almost ayear, in part due to the need to educate brokers and clients.Today, that awareness already exists when companies begin the RFPprocess, "and there is much greater buying activity than we've everseen," says Ziad Kubursi, senior vice president and head ofmanagement and professional liability at Philadelphia InsuranceCos. Kubursi adds that Philadelphia is seeing double-digit salesgrowth in the line.
|INSUREtrust, a white-label distributor of cyber liabilityproducts, saw 20% growth in premium in 2013, a number consistentwith previous years—"and we've achieved 30% growth among ourtargeted classes of business," says Steven Haase, the company'spresident.
|Yet, amazingly, not every business carries cyber liabilityprotection: The Ponemon Institute estimates that about a third of600 companies (of varying size) that responded to a poll itconducted in 2013 have a cyber policy in place. Marciano says thatsome non-buying companies mistakenly believe they are already fullycovered by their CGL policies for cyber liability or don'tunderstand the breadth of coverage available in stand-alone cyberforms. Others think that their IT security technology insulatesthem from attacks.
|"Even though organizations see cyber attacks and data breachescontinuing to occur and increasing in frequency, they still think,'It can't happen to us.' That's naive," Marciano says.
|"For some companies, it's a budget issue," says Tracie Grella,global head of professional liability at AIG. "Other companiesstruggle in the decision process to get their arms around thedifferences in coverage from carrier to carrier, while others arestill trying to assess their exposure to cyber loss."
|"There are two types of organizations—those that have had a[data] breach and know it, and those that have had a breach anddon't know it yet," says Richard Betterley, president of BetterleyRisk Consultants Inc.
|Producer Opportunity?
|Patricia A. Borowski, senior vice president at the NationalAssociation of Professional Insurance Agents, says that there is anopportunity for agents and brokers to market cyber liability byeducating customers about the gaps in standard liability forms.
|"Even among large mid-market insureds, there is a huge uptickthat has to happen in terms of their attention to the real scopeand detail of this exposure. This is even more the case withsmaller commercial accounts," she says.
|
Ken A. Crerar, president and CEO of the Council of InsuranceAgents & Brokers, and NU P&C advisory board member, saysthat while there has been "more talk than action" among small- andmedium-sized businesses around cyber insurance, he agrees that themarket presents a significant growth potential for agents.
|"The year ahead should give way to a much more proactive versusreactive space," he says.
|Capitalizing on that opportunity requires articulating thedifferent types of risks small businesses face as well as differentproducts available to small businesses. "Brokers can continue tohelp ramp up awareness and education of clients by facilitating theinput of technical specialists into the dialogue who can showcasethe layers of risks across businesses," Crerar adds.
|However, Borowski believes the tipping point in cyber purchasingwill ultimately come not through broker outreach, but by thegrowing recognition of risk across the business community.
|"While PIA members can help their customers better understandcyber issues and demonstrate how the available coverage can betterprotect them from exposure and losses, customers must have alsogained an awareness of these matters independent of insurancecarriers or their agents," she says, adding that recent newsstories regarding massive personal data breaches is helping toincrease awareness of these risks to all businesses.
|Still a Buyer's Market
|The cyber liability market remains highly competitive, withcarriers still fighting over market share. Rates are stable, andbrokers report capacity of up to $20 million with any one carrierand the ability to create $100 million coverage towers. And ascompetition remains high, underwriters are finding it increasinglydifficult to exercise rigor in the underwriting process.
|"It's definitely become easier to acquire the coverage," Haasereports. "Companies are offering simpler application forms and amore buyer-friendly process."
|Kubursi recalls that when the coverage was first offered in themarket in the early 2000s, underwriting was an involved process,involving on-site visits and interviews with clients' technologyofficers to understand the controls and safety. That's no longerthe case. "Because the loss experience on the product is veryfavorable, underwriting diligence has dwindled to virtually nothingat some companies," he says.
|Betterley reports working with one carrier that used to have 100questions on its cyber liability application. Today, they have 10,Kubursi says. "When they tried to get answers to more questions,brokers simply took the business elsewhere.
|"There are still two extremes in underwriting—from onerous tolenient—but most companies are toward the lenient side," hecontinues. "We are somewhere in the middle. I do think theunderwriting will become more rigorous across the market in thewake of high-profile breaches over the past year and as lossesincrease."
|Carriers are jockeying to compete not only thorough competitivepricing and streamlined underwriting, but with coverage and productdifferentiation.
|"Cyber liability" is a catch-all term for insurance thattypically includes a mix of third-party liability coverage fordamages suffered due to loss of data, first-party coverage forresponse and remediation costs, and coverage for fines andpenalties. Beyond those fundamental coverages, policies can includebusiness income, intellectual property, errors and omissions, andmore.
|"The scope of coverage continues to expand, and what is alreadya broad product is getting broader," says Thomas Herendeen, vicepresident of management and professional liability for PhiladelphiaInsurance Cos.
|Philadelphia's original cyber form has been enhanced over theyears to offer coverage for regulatory fines and penalties,business income and extra expense, and extortion. Endorsementsprovide coverage for risks such as corporate confidentialinformation loss, breach of private information related to minorsand expanded crisis-management costs.
|Insurance carriers also include more value-added services totheir products, including cyber security tool kits, training "andother things to help companies understand and manage risk," saysMarciano.
|In 2013, AIG completed a major enhancement of its CyberEdgeproduct, adding an array of risk-management tools to the third- andfirst-party coverage the product had provided. "We conducted asurvey of customers, and 80% of risk managers felt that one oftheir biggest challenges was keeping up with changing cyber riskand emerging threats," Grella says.
|Any business, not just AIG customers, can access information oncyber risk through the CyberEdge Mobile App for iPad that providesnews from around the world and a continuously updated breach mapthat shows hacking hotspots across the globe. AIG customers thatgenerate more than $10,000 in cyber premium also have free accessto the CyberEdge Risk Tool, which provides resources for security,training, and compliance, as well as an AutoShun hardware devicefrom RiskAnalytics.
|The AutoShun device is installed on a customer's network anduses proprietary technology to prevent communication with known"bad" IP addresses. The list, which Grella says is updated every 10minutes, "gives businesses protection against communicating withbad IP addresses that is much more current than a typical firewallprovides."
|In 2013, 170 customers signed up for the Risk Tool or anAutoShun device, a number that was in line with AIG's expectations.Betterley expects the amount and depth of value-added servicesoffered by insurers to continually increase.
|"Customers are looking not just for access to information, butanswers to questions," he says. "Most organizations don't have achief privacy officer, so having an outside resource to bounceplans and ideas off of, as happens with other lines of insurancesuch as EPLI, will be the next evolution of service in the cyberworld."
|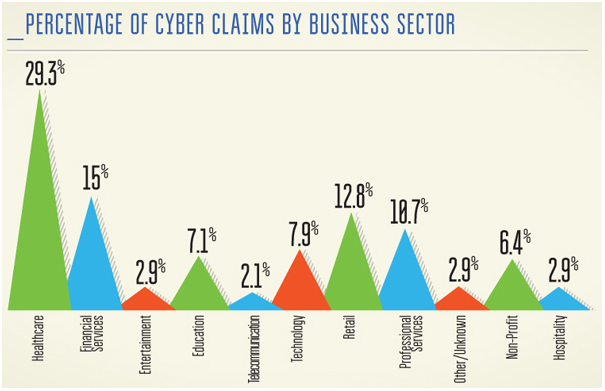
Source: NetDiligence® 2013 Cyber Liability & Data BreachInsurance Claims Study
|New Threats Raise Stakes
|In managing cyber risk, businesses must address securityconcerns such as lost devices, unencrypted data and careless userbehavior. At the same time, they must contend with new threats,including hackers' growing sophistication and organization.Increasingly, geopolitical forces are engaged in cyberterrorism.
|"Hackers aren't necessarily persons or even groups of persons.They can be machines, often funded by criminal organizations," saysBryant G. Tow, a partner at Vaco Risk Solutions in Nashville.
|Evidence is also mounting that there is an ongoing, organizedassault against U.S. retailers. In addition to Target, NeimanMarcus reported a breach of more than one million credit cards inlate 2013. Michaels Stores advised customers in January 2014 offraudulent activity that the Secret Service is investigating. Thesame month, HasbroToyShop.com was hacked, resulting in shoppersbeing redirected to a malware site.
|Companies also deal with new types of hacking activity. Thatincludes crypto-locking, where hackers prevent access to acompany's own data and threaten to destroy the data unless a ransomis paid.
|"Crypto-locking is a huge concern, but something that companiesquite frankly haven't gotten their arms around yet," says MattPrevost, assistant vice president in Philadelphia Insurance'smanagement and professional liability division.
|Also, Microsoft's announcement that it will no longer supportWindows XP effective this April has created significantvulnerability potential for companies large and small that stilluse it.
|"XP makes up a little over 20% of the operating system market,"says Tow, who expects hackers to aggressively exploit systems thatwill no longer be regularly patched.
|"The bad guys won't stop trying to find holes in it. I would sayyou probably have a month at best after support ends before you aregoing to be significantly vulnerable if you use XP, and a fewmonths until you're critically vulnerable," he predicts. "Therereally is no choice for companies but to upgrade or switchoperating systems on or before the deadline if possible."
|Claims Increasing, But Market HoldingSteady
|With increased breach activity and the growing use of cybercoverage, it follows that insurers would be handling more losses.INSUREtrust, for one, reports more than one breach incident a week,a frequency that Haase expects to grow.
|"One of the problems with breaches is companies often don't knowimmediately that they've been compromised unless a third partytells them, so it can take quite a while for claims to develop," headds.
|At AIG, says Grella, "We're seeing about a breach per day. We'redefinitely busy in claims."
|According to the Ponemon Institute, the breach cost percompromised record is $188. In the latest study by NetDiligence ofcyber claims paid by insurers, the average claim was $954,253,which included legal settlement, legal defense and crisis-servicecosts.
|"There is no such thing as a breach that costs $50,000 toresolve," says Kubursi in Philadelphia.
|Yet despite rising claim frequency, insurers report favorableexperience on the line. As a result, industry observers expect thehighly competitive market to continue for the foreseeablefuture.
|"I have no idea when the market will turn. It seems thatcoverage gets broader every year," Haase says. "Like any newer lineof business, eventually critical mass will be reached in cyberclaims experience, and companies will have to reassess howaggressively they underwrite and price coverage."
Want to continue reading?
Become a Free PropertyCasualty360 Digital Reader
Your access to unlimited PropertyCasualty360 content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- All PropertyCasualty360.com news coverage, best practices, and in-depth analysis.
- Educational webcasts, resources from industry leaders, and informative newsletters.
- Other award-winning websites including BenefitsPRO.com and ThinkAdvisor.com.
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.








