As identity thieves continue to evolve their malicious craft,professionals in the risk management field are preparing for theimplementation of the “Red Flags Rule.”
|Beginning June 1, 2010, the Federal Trade Commission willenforce new regulations requiring financial institutions andcreditors to implement a program that identifies and detects thewarning signs of identity theft.
|Originally, the FTC set the implementation deadline for Nov. 1,2008, later extending the date to May 1, Aug. 1 and then to Nov. 1,2009. The FTC delayed the deadline for a fourth time and is now setfor June 1, 2010.
|The deadline was extended to provide sufficient opportunity tocontinue to educate and help creditors and financial institutionsdevelop and implement formal identity theft programs.
|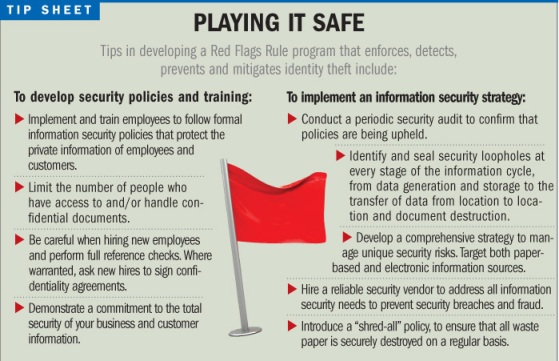
The question now is whether organizations covered by the RedFlags Rule will be prepared to comply with the new regulations whenthe latest implementation deadline arrives.
|Organizations must implement programs to protect themselves andtheir customers from breaches of data security.
|According to a study by Javelin Strategy & Research, in2007, 8.1 million Americans were victimized by identity fraud, andthe attacks continue today. Ponemon Institute's fourth annual “U.S.Cost of a Data Breach Study” indicates that the highest-impactsecurity incidents often originate from within organizations.
|Nine out of every 10 risk managers may be aware of theimportance of digital security. In one high-profile instance, amajor retail company experienced a massive security breach, whichjeopardized 45.7 million credit and debit cards. The breachoccurred after a hacker reportedly gained access to customers'credit card data and drivers' license information.
|While many risk managers may focus on digital securitypractices, some may make million-dollar mistakes by overlooking theimportance of keeping confidential paper documents secure.
|For instance, confidential information on a single documentrecently cost a large nonprofit association in Washington, D.C.more than $100,000. The breach occurred when a document containingconfidential employee life insurance information was hand-deliveredto the organization's broker, and the broker's temporary employeeproceeded to steal and sell the information.
|The case resulted in the theft of several employees' personalinformation and severe costs in legal fees and reputation for theorganization.
|How should risk managers prepare for the Red Flags Rule?
|The first step risk management professionals should take to helptheir organizations assure compliance is to conduct a loss controlassessment.
|By performing a focused evaluation of their company'soperational risks, the risk manager can identify common breachpoints in the major functions of the organization. Once these risksare identified, the risk manager can begin developing acomprehensive plan to ensure the organization is secure.
|The Red Flags Rule applies to state or national banks, savingsand loan associations, mutual savings banks, credit unions, and anyother individuals or organizations that, directly or indirectly,hold a “transaction account.”
|Organizations covered by the Red Flags Rule must be prepared tocomply with the new standards to avoid costly fines, regulatoryenforcement actions and the risk of customer identity theft.
|Risk managers can help organizations achieve compliance byenforcing security measures, such as using an outsourcedinformation destruction provider and ensuring all confidentialdocuments are disposed of properly.
|Timely and frequent document destruction is an excellentpreventive measure to help mitigate identity theft, bysignificantly reducing the risks of sensitive documents fallinginto the wrong hands.
|Additionally, shredding all confidential waste paper intounrecognizable confetti which can be recycled into new paperproducts reduces the negative environmental impact of theorganization.
|Colette Raymond is executive vice president ofoperations at Shred-it North America, based in Toronto, Canada. Formore information, visit www.shredit.com.
Want to continue reading?
Become a Free PropertyCasualty360 Digital Reader
Your access to unlimited PropertyCasualty360 content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- All PropertyCasualty360.com news coverage, best practices, and in-depth analysis.
- Educational webcasts, resources from industry leaders, and informative newsletters.
- Other award-winning websites including BenefitsPRO.com and ThinkAdvisor.com.
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.








