The WannaCry attack is evidence of a meaningful evolution in ransomware, which has strategic implications on cyber attack patterns and, subsequently, insurance coverages and aggregation risk.
There are several motivations at play for cyber attackers, but the greatest and most influential incentive is making money — and using ransomware to block access to enterprise computer systems until a payment is made is proving more fruitful for hackers than targeting private data records. It also means that businesses who have no data records are no longer a lower hazard group.
|The evolution of ransomware
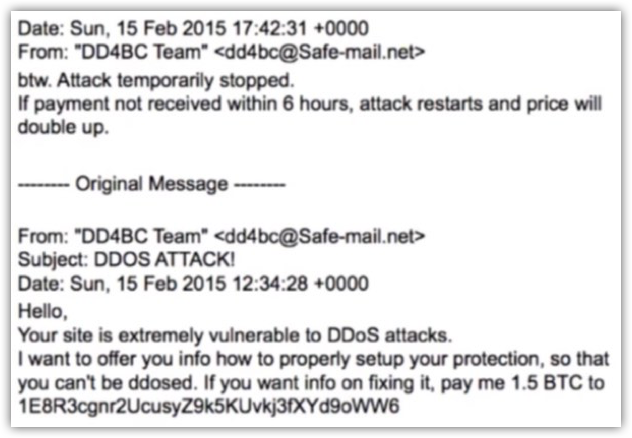
Ransomware started to gain meaningful traction in 2013 with the introduction of encryption malware like Cryptolocker, which targeted PCs mostly through phishing campaigns. It was only a matter of time until hackers discovered how to extend ransomware to other types of attacks or asset takeovers.
Recommended For You
Want to continue reading?
Become a Free PropertyCasualty360 Digital Reader
Your access to unlimited PropertyCasualty360 content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Breaking insurance news and analysis, on-site and via our newsletters and custom alerts
- Weekly Insurance Speak podcast featuring exclusive interviews with industry leaders
- Educational webcasts, white papers, and ebooks from industry thought leaders
- Critical converage of the employee benefits and financial advisory markets on our other ALM sites, BenefitsPRO and ThinkAdvisor
Already have an account? Sign In Now
© Touchpoint Markets, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more inforrmation visit Asset & Logo Licensing.